Introduction

Phishing is a type of social engineering in which an attacker sends a false message, most commonly via email, to deceive a victim. As of 2020, phishing it is by far the most common cyber-criminal attack.
Phishing attacks have become increasingly sophisticated, and they frequently appear to be a carbon copy of the site being targeted. Legislation, user training, public awareness, and technical security measures are all attempts to prevent or mitigate the impact of phishing incidents. In 2020, the FBI’s Internet Crime Complaint Center recorded more phishing incidents than any other type of computer crime.
The term “phishing” was first used in the hacking toolkit AOHell by Koceilah Rekouche in 1995. The term is a leetspeak variant of fishing that was most likely influenced by phreaking. It refers to the use of increasingly sophisticated lures to “fish” for sensitive information from users.
Phishing variants
Due to the increasing trend of Phishing attacks and different devices used by consumers a number of attack variants have started to surface including the following.
Email phishing
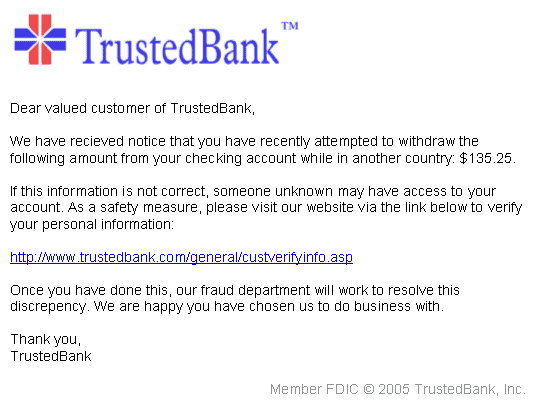
(Example of what a phishing email can look like)
Email is the most common vector for Phishing attacks and is typically performed en mass by an attacker as they send thousands or even hundreds of thousands of emails to as many people as possible in an attempt to trick some into opening links. Banks and financial services, email and cloud productivity providers, and streaming services are all common targets for impersonation.
Attackers may use the credentials obtained to steal money directly from a victim. On underground markets, compromised user accounts are typically sold directly to buyers, these attacks often have very little personalization and attempt to mimic a popular service such as PayPal or a streaming service like Netflix.
AGR Technology can help implement systems such as MailGuard which are very effective at mitigating many common phishing attacks.
Spear phishing
Unlike the original type of Phishing Spear Phishing is much more creative and very targeted to the victim or target organization. These types of attacks are sent to far fewer people and are very effective due to the information researched prior by the attacker such as the Operating System used, services used and other information which will make the email or message more convincing.
A hacker group known as Fancy Bear targeted email accounts associated with Hillary Clinton’s 2016 presidential campaign with spear phishing tactics. They targeted over 1,800 Google accounts by impersonating Google and threatening specific users using the accounts-google.com domain name.
These types of attacks are usually aimed at CEO’s of large companies or executives with access to sensitive information in large enterprises like banks or medical companies.
Vishing
The use of telephony and VOIP systems to conduct phishing attacks is known as voice phishing or vishing for short. Attackers will play automated recordings claiming fraudulent activity on victims’ bank accounts or credit cards.
The victim is then instructed to dial a number controlled by the attackers, which will either automatically prompt them to enter sensitive information in order to “resolve” the alleged fraud.
Defense mechanisms
Staff training
By far the best way to protect against the majority of phishing attacks and mitigate the risk is for organizations to train their staff on ways to spot attacks so they can avoid falling victim.
In most cases if you have a suspicious email if you hover your mouse over the link and look at the bottom of the screen a preview of the link destination will appear.
If the destination is different to the link text then it is a strong chance that the link is malicious and should be avoided.
Multi-factor authentication
Another defense mechanism against Phishing attacks is to implement Multi-factor authentication or 2FA for short. This will require a code to be entered after a username and password is entered to successfully login to an account.
If enabled an attacker would also require the code to login to the account even if they managed to acquire the username and password from the victim.
In the event credentials were entered this would give some time to quickly login and change the password safely before the attacker can gain access due to the extra requirement to login.
Email security & anti-malware software
Another method to help mitigate these attacks is to use dedicated email security software alongside an updated on-demand anti-virus & anti-malware program to actively protect your computer.
AGR Technology offers email hosting with advanced spam protection to help keep you safe. We can also help implement additional security measures to protect against other email based attacks.
FAQs about Phishing:
How can I identify a phishing attempt?
Phishing efforts frequently have a sense of urgency, asking sensitive data or login credentials. In emails or communications, keep an eye out for misspelled words, odd sender addresses, and questionable links. Always double-check senders and avoid clicking on unknown links or downloading attachments.
What actions should I take upon receiving a suspicious email?
When confronted with a dubious email, avoid clicking links or downloading attachments. Verify the sender’s identification independently through official methods. Contact the alleged sender via established contact channels. If phishing is proven, notify the appropriate authorities or your IT department.
What measures can I take to defend against phishing attacks?
To bolster your defenses against phishing:
- Be wary of unexpected emails, particularly those seeking sensitive details
- Validate sender email addresses for legitimacy
- Hover over links to preview actual URLs before clicking
- Steer clear of unknown attachments and links
- Maintain up-to-date software and security applications
- Educate yourself and others about phishing tactics to boost awareness
How does spear phishing differ from regular phishing?
Spear phishing targets specific individuals or organizations by employing personalized messages. Attackers gather victim information to craft convincing messages, making detection more challenging due to the relevance and credibility of the content.
What immediate steps should I take after falling for a phishing scam?
If you have been duped by a phishing scam, follow these steps:
- Change any compromised passwords as soon as possible and replace with secure passwords
- Notify your financial institution if financial information has been compromised
- Scan your computer for viruses and other malware
- Keep an eye on your accounts for any strange activity
- Inform your IT department or the appropriate authorities about the event
- Learn from the experience to improve your phishing awareness in the future
To avoid phishing attacks, it is critical to remain aware and practice healthy online habits.
Conclusion
We hope you found this page to be helpful; if so, please share it on social media or with someone you think would benefit from it. Also follow us on social media to keep updated with new content.
AGR Technology is a privately owned Australian company that offers a variety of digital services to other companies, including digital marketing, software development, and web design and hosting.
Learn more about our services by visiting our blog or watching our videos.
Related links from our glossary:
High-quality VPNs for Australians
VPN services to secure your connection when using P2P Filesharing
Citation(s):
(2004). Phishing [Online]. Wikipedia. Available at: en.wikipedia.org/wiki/Phishing (Accessed: 30 May 2021).
![logo-new-23[1] logo-new-23[1]](https://agrtech.com.au/wp-content/uploads/elementor/thumbs/logo-new-231-qad2sqbr9f0wlvza81xod18hkirbk9apc0elfhpco4.png)