Introduction

The study of secure communication techniques in the presence of adversarial behavior is known as cryptography. It entails creating and assessing protocols to keep third parties or the general public from reading private messages.
Modern cryptography is a multidisciplinary field that integrates mathematics, computer science, information security, electrical engineering, digital signal processing, and physics. It is used in electronic commerce, chip-based payment cards, digital currencies such as Cryptocurrencies, computer passwords, and military communications.
Cryptography methods are built with computational hardness assumptions in mind, making them difficult to break in practice. Theoretical developments and quicker processing technologies, on the other hand, necessitate ongoing reevaluation and adaptation.
The rise of cryptography has prompted legal concerns, including potential espionage and insurrection, as well as digital rights management and copyright infringement conflicts.
Terminology and background

The term “cryptograph” first appeared in the nineteenth century, in Edgar Allan Poe’s “The Gold-Bug.” The primary focus of cryptography has been on encryption, which converts plaintext into incomprehensible ciphertext, and decryption, which reverses the process. A cipher, often known as a cypher, is a pair of algorithms that perform encryption and decryption.
The key is a secret known only to the communicants that is required to decrypt the ciphertext. A cryptosystem is an ordered list of finite potential plain texts, cypher texts, keys, and the encryption and decryption techniques that correspond to each key. Keys are crucial both formally and practically, because ciphers with fixed keys are easily broken.
Many types of technologies old and modern have made use of Cryptography techniques to facilitate secure communications. For example Cryptocurrency exchange platforms in Australia, Crypto apps for Hong Kong, New Zealand, Norway, and Dubai prioritize strong security measures to protect user assets and transactions. They secure user data, including personal information and transaction details, using cryptography, the fundamental technology of cryptocurrencies. They establish encrypted connections using cryptographic protocols such as Secure Socket Layer (SSL) and Transport Layer Security (TLS), which prohibit interception and tampering.
MFA/2FA techniques, which combine a user’s known password, device, and Biometric data, give an additional layer of security to user accounts. Furthermore, these platforms incorporate advanced cryptographic techniques such as public and private key pairs, with public keys used to receive cash and private keys used to authorize transactions. These keys are securely stored in cold wallets, limiting the danger of illegal access and theft.
Cryptosystems are classified into two types: symmetric and asymmetric. In symmetric systems, the same secret key encrypts and decrypts a message, allowing for speedier data handling. Asymmetric systems encrypt a message with a public key and decrypt it with a related private key, allowing parties to communicate securely without the need for a shared secret key. In practice, asymmetric systems are used to exchange a secret key, and secure communication is carried out utilizing that key via a more efficient symmetric system.
Diffie-Hellman key exchange, RSA, ECC, and post-quantum cryptography are all examples of asymmetric systems. Insecure symmetric algorithms include children’s language tangling techniques and older cryptographic schemes, while secure symmetric algorithms include the widely used AES (Advanced Encryption Standard).
Cryptography is the process of replacing a unit of plaintext with a code word, whereas Cryptanalysis is the study of ways for extracting encrypted data without access to the key. In English, the terms “cryptography” and “Cryptology” are interchangeable, with some languages incorporating Steganography. Cryptolinguistics is the study of language properties such as frequency data and universal patterns, which is especially important in military intelligence applications for deciphering foreign communications.
History
Cryptography, which began with message confidentiality, now includes techniques for message integrity checking, sender/receiver identity authentication, digital signatures, interactive proofs, and secure computation, with the goal of ensuring the confidentiality of communications for spies, military leaders, and diplomats.
Classic methodologies
Transposition ciphers, which alter the order of letters in a message, and substitution ciphers, which systematically substitute letters or groups of letters with other letters or groups, are examples of classical ciphers. Simple versions of either have never provided much privacy from cunning opponents. The Caesar cipher, used by Julius Caesar to communicate with his generals, and Atbash, an early Hebrew encryption, are examples of early substitution ciphers. Around 1900 BCE, the earliest known usage of cryptography is engraved ciphertext on stone in Egypt.
Classical Greeks were famous for their ciphers, such as the scytale transposition cipher, which was employed by the Spartan military. Steganography, or the practice of concealing messages in order to keep them private, was also created in ancient times. An early example is a statement tattooed on a slave’s shaved head and hidden beneath regrown hair. Invisible ink, microdots, and digital watermarks are used in modern steganography. The 2000-year-old Kamasutra of Vtsyyana in India addresses two kinds of ciphers: Kautiliyam and Mulavediya. Mulavediya employs matching letters and reciprocal ones, whereas Kautiliyam use phonetic linkages.
Sassanid Persia had two secret scripts: h-dabrya for official correspondence and rz-saharya for connection with other countries. Arabs pioneered modern cryptology by documenting cryptanalytic procedures. Al-Khalil compiled the Book of Cryptographic Messages, which contains a list of all conceivable Arabic words with and without vowels.
Classical ciphers disclose statistical information about the plaintext that can be used to decipher them. An informed attacker could break most classical ciphers after frequency analysis. The first known usage of frequency analysis cryptanalysis techniques is described in Al-Kindi’s Risalah fi Istikhraj al-Mu’amma.
Modern approaches
Modern approaches to Cryptography are mainly divided into 2 categories which are Symmetric-key Cryptography & Public-key Cryptography.
Symmetric-key approach
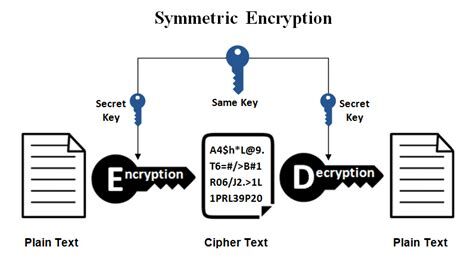
Symmetric-key cryptography is a type of encryption in which the sender and receiver use the same key. Until June 1976, it was the only sort of encryption known. Block ciphers and stream ciphers can both be used to implement symmetric key ciphers. Block ciphers encrypt input in plaintext blocks, but stream ciphers generate an arbitrarily lengthy stream of key material.
The US government has designated two block cipher designs: Data Encryption Standard (DES) and Advanced Encryption Standard (AES). Despite its retirement as an official standard, DES is still widely used for ATM encryption, email privacy, and secure remote access. Stream ciphers generate an arbitrarily long stream of key material that is merged bit by bit or character by character with plaintext. Block ciphers can be utilized as stream ciphers by creating blocks of keystreams and applying an XOR operation to each piece (bit) of the plaintext.
Cryptographic hash functions and message authentication codes (MACs) are two types of cryptographic algorithms used to verify data authenticity. To authenticate the hash value, MACs require a secret key, which prevents attacks on bare digest algorithms. Cryptographic hash functions, on the other hand, accept any length message and generate a small, fixed-length hash. The Secure Hash Algorithm series, including SHA-3, was developed by the US National Security Agency and proclaimed as the new standard in 2012. These hash functions are used to validate data from untrustworthy sources or to add security layers.
Public-key approach
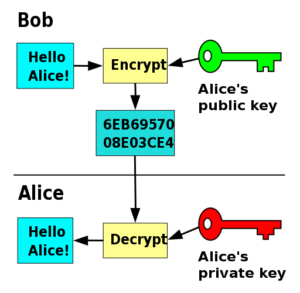
Symmetric-key cryptosystems encrypt and decrypt communications with the same key, but might utilize different keys for different messages or groups. Because each pair of communication parties must exchange a distinct key, symmetric ciphers have a disadvantage in key management.
The number of keys required grows as the square of the number of network participants, necessitating complicated key management techniques to ensure consistency and confidentiality. Whitfield Diffie and Martin Hellman proposed public-key cryptography in 1976, which employs two distinct but mathematically connected keys: a public key and a private key.
A public key system is designed so that calculating one key from the other is computationally infeasible, producing both keys covertly as an interconnected pair. Public-key cryptography has been referred to as a the most revolutionary new concept in the field since poly-alphabetic substitution emerged in the Renaissance.

Public-key cryptosystems allow the public key to be freely circulated while keeping the private key private. Through the Diffie-Hellman key exchange protocol, Diffie and Hellman showed the feasibility of public-key cryptography. In secure communications, this method is currently frequently employed.
The most often used format for public key certificates is defined by the X.509 standard. The RSA algorithm, which was created in 1978 by Ronald Rivest, Adi Shamir, and Len Adleman, is the most frequently used public-key encryption scheme. The Cramer-Shoup cryptosystem, ElGamal encryption, and elliptic curve techniques are examples of asymmetric-key algorithms.
Asymmetric key cryptography, RSA, and Diffie-Hellman key exchange are just a few of the academic developments in cryptography that cryptographers predicted in 1997, according to GCHQ. Digital signature systems are implemented using public-key cryptography and are simple for users to create but challenging for others to fake. Digital signatures can be used for signing and verifying documents since they are inextricably linked to the content of the communication. The RSA and DSA digital signature protocols are well-liked. Public key infrastructures, network security protocols like SSL/TLS, and VPNs all depend on digital signatures.
Public-key algorithms are based on the computational difficulty of “hard” problems, which are frequently derived from number theory. These algorithms are hybrid cryptosystems because they frequently involve computationally expensive operations such as modular multiplication and exponentiation. They encrypt the message with a quick, high-quality symmetric-key method, while the appropriate symmetric key is encrypted with a public-key algorithm.
Cryptographic hash functions
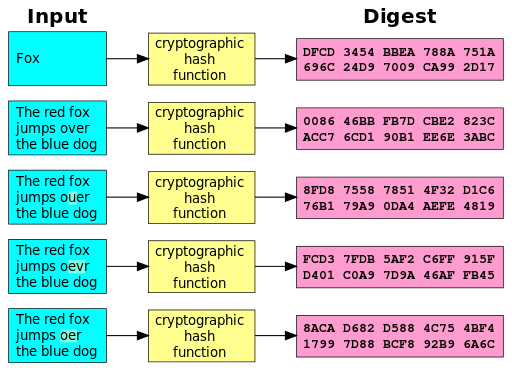
Cryptographic hash functions are cryptographic algorithms that produce and encrypt data using keys. They accept any length message as input and return a small, fixed-length hash that can be used in digital signatures. Two messages producing the same hash cannot have good hash functions.
The Secure Hash Algorithm series of MD5-like hash functions, including SHA-0, SHA-1, SHA-2, and SHA-3, was developed by the US National Security Agency. A hash function design competition was organized in order to establish a new SHA-3 national standard for the United States by 2012. Cryptographic hash functions generate hashed results that cannot be utilized to recover the original input data. They are used to validate data from an untrustworthy source or to add an extra degree of security.
One use case of Cryptographic hash functions is to secure passwords created by end-users. If the password file is compromised, storing all user credentials in cleartext can result in a catastrophic security breach. One method for reducing this risk is to only retain the hash digest of each password. To authenticate a user, the user’s password is hashed and compared to the stored hash. When password hashing is used, a password reset procedure is required; original passwords cannot be regenerated using the stored hash value.
Cryptanalysis
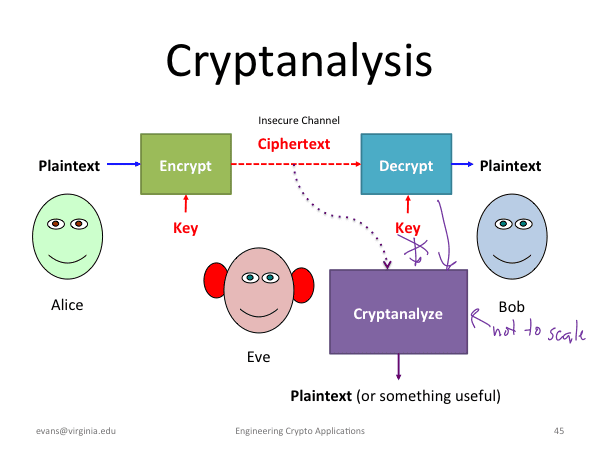
Cryptography exposes flaws in cryptographic schemes, allowing them to be subverted or evaded. Although Claude Shannon’s work at Bell Labs demonstrated that the one-time pad cipher is unbreakable, most ciphers can be broken with computing effort. There is no efficient solution for effective security. Attacks are classified depending on the attacker’s knowledge and capabilities, and errors in protocol design or implementation are critical.
Crypto systems & applications
Cryptographic primitives are used to build complicated algorithms, known as cryptosystems, that give specialized functionality while maintaining security. These systems, which include communication between parties in space or time, can be constructed from a mixture of primitive cryptosystems. RSA, Schnorr signature, ElGamal encryption, and PGP are examples of popular cryptosystems. Electronic cash systems, signcryption systems, and interactive proof systems are examples of more complicated cryptosystems.
Cryptography is a critical technique for protecting user data and preventing eavesdropping on the internet. Private key cryptography is often employed for transmission security, whereas public-key systems ensure confidentiality without the requirement of a master key or multiple keys.
Algorithms such as Bitlocker and Veracrypt, on the other hand, are not private-public key cryptography but can be set for public-private key systems. OpenSSL, a C++ opensource encryption library, provides opensource encryption software and tools for free. Because of its hardware acceleration for x86-based processors with AES-NI, AES is the most widely used encryption cipher. Because of its ARM-based nature, ChaCha20-Poly1305, a stream cipher, is often utilized for mobile devices.
Information/Cyber Security (Infosec for short)
![]()
Cryptography protects communications by encrypting them, as seen on websites such as Pretty Good Privacy (PGP Standard) and messaging programs such as WhatsApp, Signal, and Telegram. Operating systems utilize encryption to protect passwords, conceal system components, and assure the authenticity of software updates. Other systems can even encrypt whole disks, similar to BitLocker and are often included within Operating Systems natively like Windows, macOS, Linux, FreeBSD and others as well as via third party applications.
Cryptocurrencies and cryptoeconomics

Cryptographic approaches enable cryptocurrency technologies like distributed ledger technologies (e.g., blockchains) to finance cryptoeconomics applications like decentralized finance (DeFi). Cryptographic keys, cryptographic hash functions, asymmetric (public key) encryption, Multi-Factor Authentication (MFA), End-to-End Encryption (E2EE), and Zero Knowledge Proofs (ZKP) are among the major cryptographic techniques that enable cryptocurrencies and cryptoeconomics.
NSA involvement & associated controversy

In the United States, cryptography policy and research have been significantly influenced by the National Security Agency (NSA). The NSA participated in the creation of DES while IBM was developing it, and it was under consideration as a potential Federal Standard for cryptography. DES was created to be impervious to differential cryptanalysis, a potent method that both the NSA and IBM are familiar with. Due to the NSA’s request, IBM found differential cryptanalysis but kept it a secret.
The Clipper chip affair, a 1993 encryption microchip, was criticized for two reasons: the initiative violated Kerckhoffs’s Principle as it contained a special escrow key for government wiretapping, and the cipher algorithm (Slipjack) was classified, raising suspicions that the NSA had purposefully made the cipher weak to aid intelligence efforts. These incidents highlight the challenges of determining an attacker’s resources and knowledge.
Frequently Asked Questions About this topic (FAQ):

What is cryptography and why is it important?
The practice of safeguarding communication and data by transforming them into a secret code using mathematical procedures is known as cryptography. It is critical because it ensures that only authorized personnel have access to and comprehend the information, thereby protecting it against unauthorized access and potential risks.
How does encryption work?
Encryption is the process of transforming readable data (plaintext) into unreadable data (ciphertext) using a specific algorithm and a secret key. The ciphertext can only be translated back to plaintext by someone who has the associated decryption key, ensuring safe communication.
What’s the difference between symmetric and asymmetric cryptography?
Symmetric cryptography uses a single shared key for both encryption and decryption, which speeds up the process but necessitates safe key distribution. Asymmetric cryptography employs a pair of keys for encryption and decryption: a public key for encryption and a private key for decryption. It provides greater security for key exchange but is slower than symmetric cryptography.
How does public key infrastructure (PKI) work?
PKI is a framework for managing digital certificates that employs asymmetric cryptography. These certificates validate the legitimacy of persons, devices, or websites. A certificate is a digitally signed document that contains a public key and information about the owner and is signed by a trustworthy third party known as a Certificate Authority (CA).
What is a digital signature?
A digital signature functions similarly to a virtual “seal” in that it verifies the authenticity and integrity of a digital message or document. It is generated with the sender’s private key and is verifiable with the sender’s public key. If the signature is authentic, it indicates that the message has not been tampered with and was sent by the claimed sender.
Can’t encrypted data still be intercepted?
While encrypted data can be intercepted, the ciphertext appears as random characters in the absence of the decryption key. Even if intercepted, it is incredibly impossible to make sense of the data without the key. This stresses the significance of good encryption techniques and secure key management.
Are there any challenges in cryptography?
There are indeed difficulties. One difficulty is protecting encryption algorithms from more sophisticated attackers. Furthermore, controlling and protecting cryptographic keys is critical; if keys are compromised, data security is jeopardized. To respond to evolving threats, systems and algorithms must be updated on a regular basis.
Conclusion
All up Cryptography remains an important part of modern life and the internet and is a constantly evolving area as security threats become more sophisticated and the necessary methods to keep data and communications secure need to keep evolving.
We hope you found this page to be helpful, if so be sure to share it with anyone you think would find it interesting on social media.
Other relevant pages from our website:
Best VPN platforms for Australia
How to choose secure passwords
Online tool to find IP address (Show My IP)
How to remove adware from your PC
Summary of different companies, people and technologies in the Crypto industry
What are forks in Cryptocurrency?
Fintech (Financial technologies)
What is a Neobank and how does it work?
How can you accept Cryptocurrency payments on your website?
Guide to buying Bitcoin in Australia
What are some of the best Cryptocurrencies to buy based on up-to-date prices?
Blockchain Explorer Definition
Cryptocurrency Market Analysis Definition
What are Initial Exchange Offerings (IEOs)
Some of the best small business loan providers in Australia
Buyers guide to choosing the best Crypto exchanges in Taiwan
Some of the most top-rated CFD trading platforms/brokers for Dubai users
Buyers guide / Comparison of Cryptocurrency platforms for Singapore users
Source(s) cited for this page:
Cryptography. Wikipedia. https://en.wikipedia.org/wiki/Cryptography. Published November 12, 2001. Accessed August 15, 2023.
https://dictionary.cambridge.org/dictionary/english/steganography.
M. Crowley, (2004). Principles of Steganography [Online]. Available at: https://mathweb.ucsd.edu/~crypto/Projects/MaxWeiss/steganography.pdf (Accessed: 23 August 2023).
“Cryptolinguist.” Wiktionary, the free dictionary. Accessed August 23, 2023. https://en.wiktionary.org/wiki/cryptolinguist.
(2010, September 23). https://media.defense.gov/2021/Jun/29/2002752324/-1/-1/0/A_MISSION_OF_GREAT_IMPORTANCE.PDF
NIST Selects Winner of Secure Hash Algorithm (SHA-3) Competition. NIST. https://www.nist.gov/itl/csd/sha-100212.cfm. Published October 2, 2012. Accessed August 26, 2023.
Davidgothberg, Public domain, via Wikimedia Commons
[Online]. Available at: https://fsi-live.s3.us-west-1.amazonaws.com/s3fs-public/styles/820xauto/public/rsa_ms.jpg?itok=3Rxxtty1 (Accessed: 26 August 2023).
“Cryptographic hash function.” June 8, 2023. Accessed August 26, 2023. https://developer.mozilla.org/en-US/docs/Glossary/Cryptographic_hash_function.
Cryptographic hash function, Wikipedia (Jan. 23, 2004), https://en.wikipedia.org/wiki/Cryptographic_hash_function.
(2013). [Online]. Available at: http://www.cs.bc.edu/~straubin/crypto2017/heys.pdf (Accessed: 26 August 2023).
https://www.iconfinder.com/icons/7023958/download/png/512 Via https://creativecommons.org/licenses/by/3.0/
National Security Agency, Public domain, via Wikimedia Commons
Schneier, Bruce. “What Exactly Are the NSA’s ‘Groundbreaking Cryptanalytic Capabilities’?” WIRED, 4 Sept. 2013, www.wired.com/2013/09/black-budget-what-exactly-are-the-nsas-cryptanalytic-capabilities/. Accessed 26 Aug. 2023.
“Cryptography/Differential cryptanalysis.” Wikibooks, open books for an open world. Accessed August 26, 2023. https://en.wikibooks.org/wiki/Cryptography/Differential_cryptanalysis.
E. Biham, (2009). Differential Cryptanalysis of the Data Encryption Standard [Online]. Available at: https://courses.csail.mit.edu/6.857/2020/files/L05-differential-cryptanalysis-of-the-data-encryption-standard-biham-shamir-authors-latex-version.pdf (Accessed: 26 August 2023).
![logo-new-23[1] logo-new-23[1]](https://cdn-ihdfn.nitrocdn.com/eZVJvoSTyVixkEUySRKiaseNtUlmgCyu/assets/images/optimized/rev-0174fc5/agrtech.com.au/wp-content/uploads/elementor/thumbs/logo-new-231-qad2sqbr9f0wlvza81xod18hkirbk9apc0elfhpco4.png)