Introduction
Transport Layer Security (TLS) is a cryptographic protocol that provides network communications security for data transferred over a network and provides protection against attackers who may be monitoring the network for traffic activity such as login sessions. Several versions of the protocol are widely used in applications such as Email, Instant Messaging, and Voice Over IP.
It builds on the foundation of the previous SSL (Secure Sockets Layer) technology specifications created between the years: 1994, 1995, 1996 by Netscape Communications in their original web browser Netscape Navigator.
TLS (or SSL) encrypts connections to prevent eavesdropping and tampering. To communicate across a network, client-server applications use the TLS protocol. Before a connection can be turned on or off, the client must notify the server of its configuration.
For example, port 80 is commonly used for unencrypted HTTP traffic, whereas port 443 is commonly used for encrypted HTTPS traffic.
SSL/TLS technology has become the de-facto standard for websites and digital commerce for many years and is included in most servers with some web hosting providers like AGR Technology providing hosting with free SSL certificates.
The terms SSL and TLS are usually used in conjunction to mean the same thing despite there been small differences between the protocols.
Early history behind the technology/protocols

(Padlock symbol used by all major web browsers to signify a website is secured by a SSL/TLS certificate)
The Transport Layer Security Protocol (TLS) was created as a result of a collaborative effort that began in August 1986. TLS, formerly known as the SP4 protocol, it was published in 1995 as international standard ITU-T X.274| ISO/IEC 10736:1995.
In an extensive set of published papers, the program was described in September 1987 at the 10th National Computer Security Conference. It was designed to supplement the rapidly emerging new OSI internet standards in the future.
Security researchers have been working on a secure transport layer API since the early 1990s. The aim was to retrofit pre-existing network applications with security measures that would make them more secure.
This approach is similar to the Secure Network Programming (SNP) application programming interface (API), which in 1993 explored the approach of having a secure Transport Layer 1 API closely resembling Berkeley sockets.
SSL Version(s) 1.0-3.0 (Developed by Netscape)
Taher Elgamal, chief scientist at Netscape Communications from 1995 to 1998, has been dubbed the “Father of SSL” for developing the original SSL protocols. Because of serious security flaws in the protocol, SSL version 1.0 was never released. Version 2.0, released in February 1995, had several security flaws that necessitated the creation of version 3.0.
SSL version, released in 1996, represented a complete redesign of the protocol created by Paul Kocher in collaboration with Netscape engineers Phil Karlton and Alan Freier. SSL was discovered to be vulnerable to the POODLE attack in 2014, which affects all block cyphers in SSL.
Since the introduction of newer versions of TLS SSL versions 2.0 and 3.0 have been depreciated by the Internet Engineering Task Force (IETF) which is a body responsible for setting and maintaining many protocols and standards.
TLS (Transport Layer Security)
TLS didn’t appear until in 1999 as a standalone independent protocol in this document (RTF2246) and provides a fallback to SSL version 3.0 for compatibility with older web browsers.
TLS leverages a combination of symmetric and asymmetric cryptography to achieve a good balance of performance and security whilst securely transmitting data over networks.
TLS covers all aspects of the session and data been transmitted and uses stronger encryption algorithms in comparison to older SSL standards
Asymmetric encryption (public key)
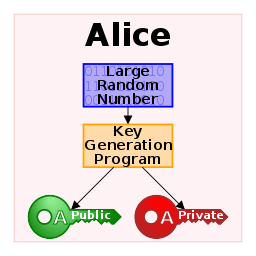
Public-key Cryptography is a cryptographic system that employs key pairs: public and private keys. Without jeopardizing security, the public key can be freely distributed. In such a system, anyone can encrypt a message using the public key of the intended receiver, but that encrypted message can only be decrypted using the receiver’s private key.
This enables server software to generate a cryptographic key for a suitable symmetric-key cryptosystem, then encrypt that newly generated symmetric key using a client’s openly shared public key.
Symmetric encryption
Symmetric-key algorithms are cryptographic algorithms that use the same cryptographic keys for both plaintext encryption and ciphertext decryption. The keys represent a shared secret shared by two or more parties that can be used to keep a private information link open.
One of the main disadvantages of symmetric-Key encryption over public-key encryption is the requirement that both parties have access to the secret key.
Certificate Authority or CA for short
In order for certificates to be trusted by different browsers and systems Certificate Authorities exist which act as validators to ensure a certificate is trusted and signed.
Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both the encryption of plaintext and the decryption of ciphertext. The keys represent a shared secret between two or more parties that can be used to maintain a private information link.
The requirement that both parties have access to the secret key is one of the main drawbacks of symmetric-Key encryption, in comparison to public-key encryption however is more convenient as the validation is done by a third party.
A digital certificate verifies the ownership of a public key by the certificate’s named subject and specifies certain expected key usages. Others (relying parties) can then rely on signatures or assertions made by the private key that corresponds to the certified public key.
Keystores and trust stores can be in a variety of file formats such as: .pem,.crt,.pfx, and.jks.
Verisign, GeoTrust, and Symantec are some examples of Certificate Authorities.
As encryption algorithms continue to develop and more security vulnerabilities are discovered TLS certificates continue to improve and as such web browsers and websites need to keep up to ensure they continue to deliver content securely to their end-users.
Conclusion
We hope you found this page to be helpful and help provide an explanation of SSL/TLS technologies. If you found it useful please consider sharing this page and following us for more updates.
Also be sure to checkout the below links to other relevant pages from our glossary and check out our blog and business service offerings for more.
Relevant pages from our technology glossary:
CDN (Content Delivery Network)
Best VPN tools for Australian consumers
Bibliography & Citation(s):
En.wikipedia.org. 2021. Transport Layer Security – Wikipedia. [online] Available at: <https://en.wikipedia.org/wiki/Transport_Layer_Security#SSL_1.0,_2.0,_and_3.0> [Accessed 25 July 2021].
Internet Society. 2021. What is TLS & How Does it Work? | ISOC Internet Society. [online] Available at: <https://www.internetsociety.org/deploy360/tls/basics/> [Accessed 25 July 2021].
“Public-key cryptography” Wikipedia, 9 Nov. 2001, en.wikipedia.org/wiki/Public-key_cryptography. Accessed 25 July 2021.
KohanX, Public domain, via Wikimedia Commons
“Symmetric-key algorithm” Wikipedia, 23 Oct. 2001, en.wikipedia.org/wiki/Symmetric-key_algorithm. Accessed 25 July 2021.
![logo-new-23[1] logo-new-23[1]](https://agrtech.com.au/wp-content/uploads/elementor/thumbs/logo-new-231-qad2sqbr9f0wlvza81xod18hkirbk9apc0elfhpco4.png)