Introduction

Peer-to-peer, or P2P, computing is a distributed application architecture in which peers—equally privileged and equipotent network participants—share tasks or workloads. In this way, a peer-to-peer network of nodes is created in which other network users can directly access resources such as computing power, disk storage, or network bandwidth without the need for central coordination. Unlike the conventional client-server approach, peers are both resource providers and consumers.
The 1999 release of Napster, a file-sharing platform, made P2P systems widely known and gave rise to new paradigms and structures in interpersonal communication. P2P, as used in a social context, describes the egalitarian social networking that has proliferated due to internet technologies.
Simple image to illustrate the structure of a P2P network:
P2P systems allowed millions of internet users to connect directly, organize groups, and work together to develop search engines, virtual supercomputers, and filesystems. P2P systems were made popular by file sharing apps like Napster. Peer-to-peer computing was first proposed in previous conversations about networking and software systems, beginning with RFC 1.
Tim Berners-Lee imagined the World Wide Web (WWW for short) as a peer-to-peer network in which each user would be an active editor and contributor, producing and linking content to form an interconnected “web” of links. The early Internet was more open, allowing packets to be sent between two workstations without the use of firewalls or other security mechanisms. ARPANET, the Internet’s forerunner, was a successful peer-to-peer network in which any participating node could request and serve material. ARPANET, on the other hand, was not self-organized and lacked context or content-based routing in addition to address-based routing.
In 1979, Usenet, an early peer-to-peer architecture, was created as a decentralized message system. It employs a client-server architecture, allowing newsgroup servers to communicate as peers. This model is also used for SMTP email, with the core network being peer-to-peer and the clients and their connections being client-server interactions.
Shawn Fanning introduced Napster, a music and file-sharing application, in May 1999, when there were millions more people on the Internet. Napster was the first peer-to-peer network, where “participating users establish a virtual network, entirely independent of the physical network, without having to obey any administrative authorities or restrictions”.
Structure of P2P networks / Network Architecture
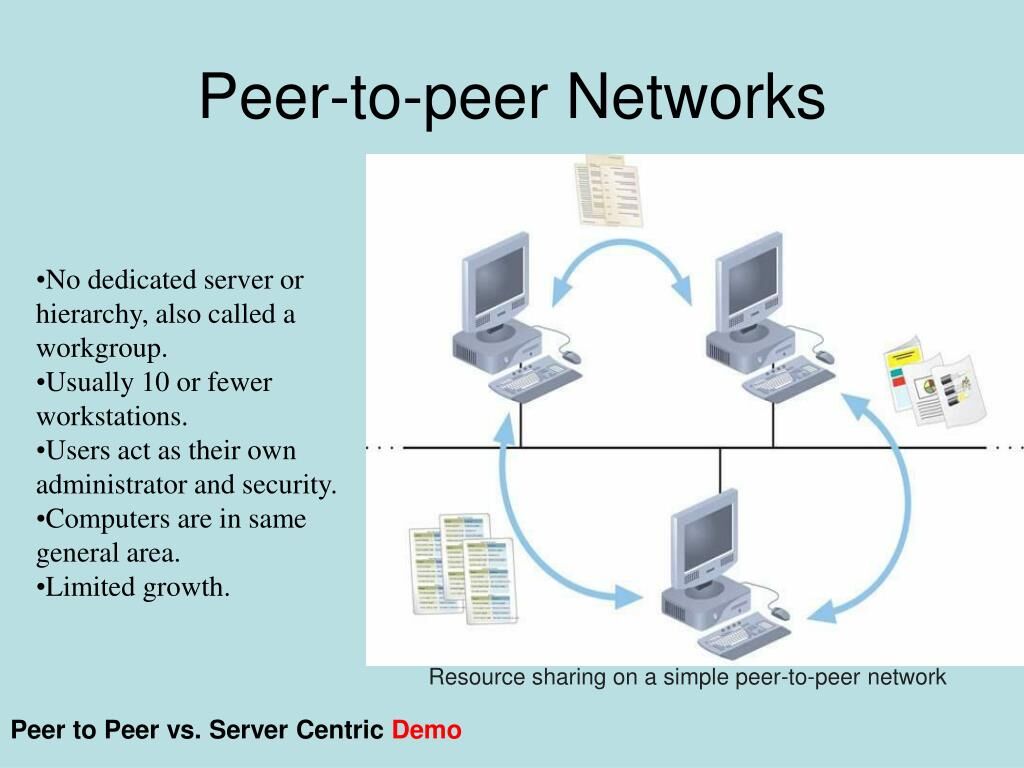
A peer-to-peer network is a network model in which equal nodes function as both clients and servers, as opposed to the client-server model, in which communication is primarily to and from a central server. The File Transfer Protocol (FTP) service is an example of this approach, in which clients initiate transfers and servers complete them.
Peer-to-peer networks present unique computer security challenges.
P2P programs, like any other type of software, might have flaws. What makes this more risky for P2P software is that peer-to-peer apps work as both servers and clients, making them more exposed to remote vulnerabilities.
Because each node is responsible for routing traffic via the network, malevolent users can launch a variety of “routing attacks” or denial of service attacks. Common routing attacks include “incorrect lookup routing,” in which malicious nodes intentionally forward requests incorrectly or return false results, “incorrect routing updates,” in which malicious nodes corrupt the routing tables of neighboring nodes by sending them false information, and “incorrect routing network partition,” in which new nodes bootstrap via a malicious node, which places the new node in a partition of the network that is populating.
Routing and resource discovery
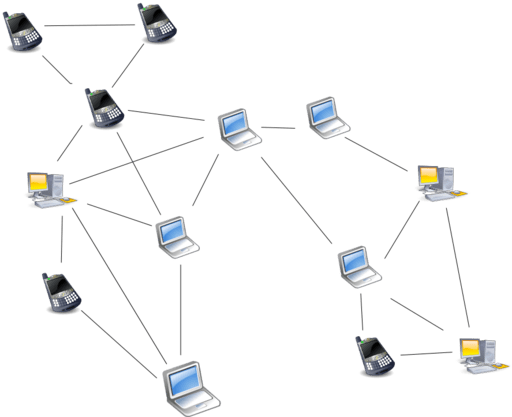
Peer-to-peer networks use a virtual overlay network on top of the physical network topology to allow peers to connect directly over logical overlay links. This enables indexing and peer finding, separating the P2P system from the physical network structure. Unstructured, structured, or hybrid networks are the three types of networks.
Unstructured network topology
The lack of structure in unstructured peer-to-peer networks like Gnutella, Gossip, and Kazaa’s overlay network enables localized optimizations and great resilience. However, this lack of structure results in restrictions, such as the requirement to flood the network with peer search requests to discover peers who have the needed data. Flooding utilizes more CPU and memory, generates a lot of signaling traffic, and doesn’t always result in a resolution. In contrast to rare data that is most likely to be unsuccessfully shared by a small number of peers, popular information is probably available at several peers.
Structured P2P networks
The overlay is organized into a certain topology in structured peer-to-peer networks, and the protocol assures that any node may efficiently search the network for a file/resource, even if the resource is highly scarce.
The most prevalent sort of structured P2P network is a distributed hash table (DHT), which uses a variant of consistent hashing to assign ownership of each file to a specific peer. This allows peers to search for network resources using a hash table: (key, value) pairs are kept in the DHT, and any participating node can efficiently obtain the value associated with a particular key.
DHT-based distributed network solutions (DHTs) are less robust in networks with large churn rates because nodes must keep lists of neighbors that meet specified requirements. High advertising expenditures, as well as static and dynamic load imbalances, are difficulties that DHTs face. Tixati, Kad, Storm botnet, and YaCy are examples of DHT-based networks. Chord, Kademlia, the PAST storage utility, P-Grid, and the CoopNet content distribution system are all research projects. DHT-based networks are also utilized in grid computing systems for efficient resource discovery, which aids in resource management and application scheduling.
Hybrid approaches to P2P networks
Peer-to-peer and client-server models are combined in hybrid architectures, with a central server supporting peer-to-peer communication. Spotify is one example. These models mix centralized functionality with node equality, and they currently outperform pure unstructured or structured networks due to decentralized aggregation-enhanced capabilities like searching.
This type of structure benefits from the increased performance by spreading the load across hundreds or even thousands of different devices globally whilst also providing the reliability of a centralized service.
Use cases & real world applications
P2P networks have found their way into a number of different use cases and applications in computing including but not limited to the following:
Cryptocurrency

Peer-to-peer (P2P) networks form the foundation of cryptocurrencies such as Bitcoin. P2P networks enable direct, secure transactions between users rather than relying on a central authority. Each network user (node) has a copy of the blockchain, a public ledger that contains all transaction records. When you send cryptocurrency, nodes verify it and add it to the blockchain via a consensus process. This decentralized model assures openness and security while eliminating the need for intermediaries such as banks. In the world of cryptocurrencies, P2P networks enable people to exchange digital currency. The peer-to-peer technique can also be integrated with a centralized network design to improve dependability and other characteristics. Many different cryptocurrency exchanges use this to enable people to buy cryptocurrency assets all over the world such as in New Zealand, Australia, Dubai and many other places.
Peer-to-peer banking and financial services

Neobanks and peer-to-peer lending platforms are game changers in the digital financial services space, encapsulating the collaborative spirit of peer-to-peer networks. As digital-only financial organizations, neobanks use technology to provide seamless and user-centric banking experiences, posing a challenge to traditional banking practices. Peer-to-peer lending systems, on the other hand, enable direct lending and borrowing between individuals while avoiding traditional financial intermediaries. Both technologies capitalize on the ability of decentralized networks to promote financial inclusion, efficiency, and accessibility. These disruptive models emphasize the evolution of financial services in the digital age toward more agile, customer-centric, and linked systems.
Distributed storage and search

P2P networks offer benefits and drawbacks concerning data availability, backup, and recovery. Administrators manage file availability in a centralized network, rendering users helpless and open to attacks from the state and other powerful entities. Although content availability on server-client networks is more stable, file sharing of less popular files is less dependable. The user base of P2P networks determines what content is available, with popular files being more readily available and reliable than those on centralized networks.
In contrast to centralized systems where administrators are in charge of data recovery and backups, P2P networks require the loss of connections between all nodes in order for data sharing to fail. P2P networks have benefits and drawbacks when it comes to data availability, backup, and recovery.
File sharing

The distribution and sharing of digital files via peer-to-peer (P2P) networking technology is known as peer-to-peer file sharing. Through the use of P2P software, which looks for linked computers on a network, users can access media files such as books, music, movies, and games. Distribution servers and end-user PCs are the nodes of P2P networks. BitTorrent protocol is an example of how the technology has changed through design stages from Gnutella. Microsoft utilizes it to distribute content for online video games and Windows 10 updates. Growing internet bandwidth, the digitization of physical media, and the capabilities of home PCs are some of the factors that have led to its broad use.
Different applications that fall into the category of file sharing that make use of P2P networks include the following:
Bittorrent
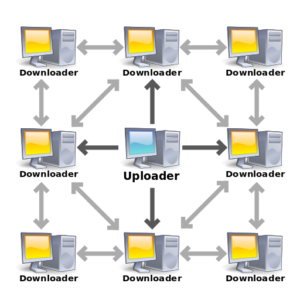
Instead of relying on a central server, the BitTorrent network uses a peer-to-peer (P2P) design in which users, or “peers,” share and receive data directly from one another. Decentralization boosts efficiency and resilience. When a user wishes to download a file, they connect to numerous peers who already have sections of the file and download them in parallel. This simultaneous downloading and uploading of portions promotes faster and wider distribution. BitTorrent also employs a tit-for-tat mechanism, in which users are incentivized to upload while downloading, thereby preserving network health and creating a cooperative sharing economy.
Bram Cohen created the popular BitTorrent protocol in 2001 to facilitate the transport of huge files, such as digital audio or video. It produces a large amount of internet traffic and accounts for 3.35 percent of the bandwidth used worldwide. There are 150 million active users and between 15 and 27 million concurrent users as of 2013. ISPs may, however, restrict its use for legal or copyright reasons, forcing users to use VPNs or seedboxes.
Gnutella
A peer-to-peer network protocol is called Gnutella. It was the first decentralized peer-to-peer network of its sort when it was founded in 2000, and other networks eventually adopted the approach.
Gnutella had 1.81 million machines in June 2005, and by January 2006, there were over three million nodes. With an estimated market share of more than 40%, it was the most widely used file-sharing network on the Internet at the end of 2007.
A distributed substitute for semi-centralized networks such as FastTrack and Napster is the Gnutella network. Early in 2001, Napster’s legal troubles made it more well-known and exposed its scaling issues. Improved scalability was made possible by modifications to the protocol, which routed search requests and responses for connected users and treated some users as ultrapeers. LimeWire Basic, a Gnutella client, went free and open source at the end of 2001. With the advent of Gnucleus, a free and open source Gnutella client, Morpheus published a new client in February 2002, abandoning its FastTrack-based peer-to-peer software. The term “Gnutella” is a combination of the Italian hazelnut-flavored spread Nutella and the open protocol that is utilized by a number of clients. Gnutella is not connected to either the GNU project or GNUnet, the project’s peer-to-peer network.
After splitting off from the original Gnutella project and adopting the Gnutella name, another protocol emerged called G2. The name, according to detractors, suggests supremacy and might spark a flame war. G2 has inadequate documentation, and Gnutella bootstraps G2 peers using the Gnutella network. The Gnutella network may be burdened by the Shareaza client’s repeated retries of searches. Since 2002, both protocols have had substantial modifications, with G2 providing a more effective hybrid search than Gnutella. Compared to G2, Gnutella has a larger user base. It is difficult to compare the protocols since end users may be impacted by the client they choose on either network.
Kazaa

Sharman Networks ran Kazaa Media Desktop, a peer-to-peer file sharing program licensed by Joltid Ltd. Later, Atrinsic, Inc. obtained a license to operate it as a legitimate music subscription service through August 2012. Using Kazaa, users could share documents, films, apps, and MP3 music files online. But copyright complaints were filed against it, and it was packaged with adware.
BlueMoon Interactive’s Estonian coders created Kazaa and FastTrack, which were sold to Swedish entrepreneur Niklas Zennström and Danish programmer Janus Friis. Kazaa, launched in March 2001 by the Dutch business Consumer Empowerment, allowed users to make calls by directly connecting with one another. Initially, some users used the Morpheus client application, which was previously available from MusicCity. However, the official Kazaa client gained popularity. When Morpheus creators failed to pay license costs in February 2002, Kazaa developers employed an automatic update feature to block Morpheus clients, resulting in Morpheus becoming a client of the Gnutella network.
The platform was an early P2P file sharing application however wasn’t fully decentralized and had a semi-centralized search indexing system.
Tor (The Onion Router)

Tor is a free, open-source program that allows for anonymous communication via a global volunteer overlay network. It safeguards personal privacy by masking location and usage from network monitoring and traffic analysis. Tor exit nodes allow for private communication via an encrypted P2P network architecture.
Tor, a computer security system, was created in the mid-1990s by workers of the US Naval Research Laboratory, mathematician Paul Syverson, and computer scientists Michael G. Reed and David Goldschlag, to safeguard American intelligence communications online. Tor employs encryption at the application layer of the communication protocol stack, which is stacked in the manner of an onion. The Onion Routing project’s alpha version was released in 2002. A year later, the first public release took place. Tor code was released under a free license by the Naval Research Laboratory in 2004, and its development was financed by the Electronic Frontier Foundation. The Tor Project was launched in 2006, and numerous Tor flaws have been uncovered and exploited.
eDonkey network

US developers Jed McCaleb and Sam Yagan founded the eDonkey Network, sometimes referred to as the eDonkey2000 network or eD2k, in 2000. It is a decentralized, server-based peer-to-peer file sharing network. Large file sharing and long-term file availability are its best uses. The network’s server component is proprietary freeware, divided into two families: eserver and the original MetaMachine server. As of 2008, the eserver family is still being developed and supported, and nearly all eD2k servers are using this server software. eDonkey2000 and eMule, a free Windows application licensed under the GNU GPL, are included in the client portion. Although it isn’t officially published, eMule and eserver communicate via the eD2k protocol.
eDonkey client applications establish connections with the network to exchange files, whereas eDonkey servers serve as central communication points for clients, enabling users to discover files within the network. Clients and servers are compatible with various operating systems such as Windows, Mac OS X, Linux, and other Unix-like systems. By installing an eDonkey server program on a computer connected to the Internet, any user can contribute a server to the network.
Napster

Shawn Fanning and Sean Parker launched Napster, a stand-alone peer-to-peer file sharing service that ran from June 1999 to July 2001. The brand survived after being shut down by a court order and having its assets liquidated and acquired by other businesses through bankruptcy proceedings.
Napster, a peer-to-peer file-sharing application, debuted in 1999 with a concentration on the dissemination of digital audio files. Shawn Fanning and Sean Parker founded it, but it ran into legal problems over copyright infringement and declared bankruptcy in 2002. Gnutella, Grokster, Limewire, Frostwire, Freenet, FastTrack, and Soulseek were among the decentralized efforts that followed. Due to copyright difficulties, certain services and software were also shut down or altered. Roxio purchased Napster’s assets and relaunched it as an online music retailer. Best Buy later integrated Napster with Rhapsody, rebranding it as Napster again.
Similar to Kazaa it wasn’t fully P2P and employed a semi-centralized infrastructure for searching files that were then spread and stored across different computers on the network made up of lots of different users.
Distributed research efforts
(Image of Seti@home project)
P2P networks have been able to help facilitate many different research projects that would otherwise require very expensive and vast computing resources to process calculations. By crowdsourcing this with a decentralized network that is globally distributed research projects can take advantage of immense amount of processing power from thousands of computers which aggregated together can match powerful servers and expensive processors.
One project that has done this and been around for many years is called Seti@home by the Berkley University in California which aims to conduct space research to find other planets and lifeforms. Following Great Internet Mersenne Prime Search (GIMPS) in 1996 and distributed.net in 1997, the SETI@home software, published on May 17, 1999, is the third large-scale use of volunteer computing over the Internet for scientific purposes. It is the third major computing effort devoted to the study of interstellar space phenomena.
The project stopped distributing fresh work to SETI@home users in March 2020, instead focused on studying and interpreting data from the previous 20 years. However, the team left the door open for volunteer computing to resume using data from other radio telescopes. The science team has evaluated the data and deleted noisy signals with the Nebula tool as of November 2021, and will select the top-scoring 100 or more multiplets to be studied with the Five-hundred-meter Aperture Spherical Telescope.
Content Delivery Networks (CDNs)
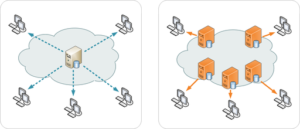
Content Delivery Networks or CDNs for short make use of Peer-to-peer technologies and help websites handle more traffic by distributing the load across different servers or in some cases end-user devices across the world. Typically the content is stored on servers in specific countries and then served based on the location of the visitor in order to be more efficient.
For example a server streaming video content could have a server in Germany storing copies of its files so if someone from Belgium where to visit the website they would receive a copy from the German server which would be much closer to them as opposed to going straight to the original source which might be half way across the world.
CDN platforms can also offer security benefits and help mitigate certain types of attacks such as DDoS attacks (Denial of service) as well as offer other types of website firewall solutions to filter out malicious traffic.
Conclusion
We hope you found this content on our glossary to be helpful and learnt more about this type of network architecture and its benefits as well as drawbacks. Be sure to share it with anyone you think would find it interesting and check out some other pages below for other topics on our technology glossary.
You may also like these pages on our website:
What are Privacy Coins and how do they work?
Citation(s) / Bibliography:
The 360 Degree, CC BY-SA 4.0, via Wikimedia Commons
(2001, September 28). Peer-to-peer. Wikipedia. https://en.wikipedia.org/wiki/Peer-to-peer
“Peer-to-peer file sharing” Wikipedia, 5 Mar. 2006, en.wikipedia.org/wiki/Peer-to-peer_file_sharing. Accessed 21 Oct. 2023.
[Online]. Available at: https://image2.slideserve.com/4254319/peer-to-peer-networks-l.jpg (Accessed: 21 October 2023).
Mesoderm, CC0, via Wikimedia Commons
“429 Too Many Requests.” June 14, 2012. Accessed October 21, 2023. https://web.archive.org/web/20131006022409/http://www.p2pnews.net/2012/06/14/art-thou-a-peer/.
upload.wikimedia.org/wikipedia/commons/7/79/Structured_%28DHT%29_peer-to-peer_network_diagram.png. Accessed 21 Oct. 2023.
Namazu-tron, LGPL, via Wikimedia Commons
SETI@home. Wikipedia. https://en.wikipedia.org/wiki/SETI%40home. Published September 2, 2003. Accessed October 21, 2023.
The original uploader was ACNS at English Wikipedia., CC BY-SA 3.0, via Wikimedia Commons
“Gnutella”, Wikipedia. 13-July-2001. [Online]. Available: https://en.wikipedia.org/wiki/Gnutella. [Accessed: 21-Oct.-2023].
external-content.duckduckgo.com/iu/?u=https%3A%2F%2Ftse1.mm.bing.net%2Fth%3Fid%3DOIP.ebfDB7DI6ZHSwq_r-zOL5wHaHd%26pid%3DApi&f=1&ipt=b6208d5193a671dd0305c49296a48bced3a9709f4007cde321bff53e1e62e6e2&ipo=images. Accessed 21 Oct. 2023.
Kazaa, Wikipedia (Sept. 28, 2001), https://en.wikipedia.org/wiki/Kazaa.
“Tor (network).” Wikipedia. December 10, 2004. Accessed October 21, 2023. https://en.wikipedia.org/wiki/Tor_(network).
(2005). eDonkey network [Online]. Wikipedia. Available at: https://en.wikipedia.org/wiki/EDonkey_network (Accessed: 21 October 2023).
Scott Martin, CC BY-SA 3.0, via Wikimedia Commons
(2003). BitTorrent [Online]. Wikipedia. Available at: https://en.wikipedia.org/wiki/BitTorrent (Accessed: 22 October 2023).
“Napster” Wikipedia, 3 Mar. 2001, en.wikipedia.org/wiki/Napster. Accessed 22 Oct. 2023.
Image by <a href=”https://pixabay.com/users/thedigitalway-3008341/?utm_source=link-attribution&utm_medium=referral&utm_campaign=image&utm_content=1583534″>Kris</a> from <a href=”https://pixabay.com//?utm_source=link-attribution&utm_medium=referral&utm_campaign=image&utm_content=1583534″>Pixabay</a>
![logo-new-23[1] logo-new-23[1]](https://cdn-ihdfn.nitrocdn.com/eZVJvoSTyVixkEUySRKiaseNtUlmgCyu/assets/images/optimized/rev-e93b6b3/agrtech.com.au/wp-content/uploads/elementor/thumbs/logo-new-231-qad2sqbr9f0wlvza81xod18hkirbk9apc0elfhpco4.png)
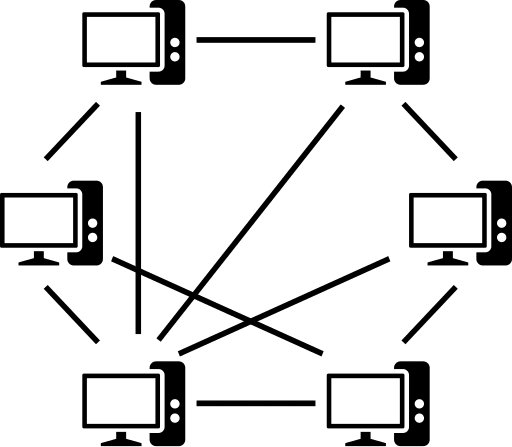
_peer-to-peer_network_diagram.png/512px-Structured_(DHT)_peer-to-peer_network_diagram.png)