Introduction
Have you ever had the frustration of downloading a file only to find that it was corrupted or you didn’t download the original.
Perhaps you went to download a piece of software and not 100% sure that your getting the official version?
This is where hashing comes in, to put it simply every file on your computer is assigned a unique ID which helps identify that file.
This is particularly relevant when it comes to software packages which often have specific hash signatures to prove they are the original version.
Other times developers will publish the original hashes for their files on the download page.
Video guide
Some common hashing algorithms include the following:
- MD5 (commonly used but not very secure)
- SHA (depreciated but more secure than MD5)
- SHA-1 (depreciated but still in use)
- SHA-256 and SHA-512 (currently secure and in use)
Hashes can be in different algorithms and each one will have a separate string of text, for more technical information refer to this page.
Why is it important to verify hashes
Whenever a file is changed the hash string will change making it very important from a security standpoint to ensure the hash you have matches with that of the original source.
Such strings are especially important when you are downloading operating systems or new software on your computer.
If the file was tampered with or damaged in transit you can verify if you have a legitimate copy and one that is complete and not corrupted.
How to get started verifying your hashes
In order to start calculating hashes head over to this page to download HashToolbox, a free opensource utility developed to easily calculate hashes.

Once downloaded open the zip and extract the files by dragging and dropping to a folder on your computer.
In the event you receive a prompt simply choose “run anyway” to launch the program.
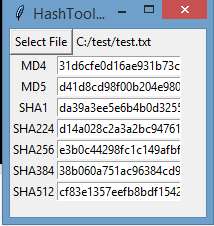
Next up choose “select file” and locate a file on your computer you wish to calculate the hash for.
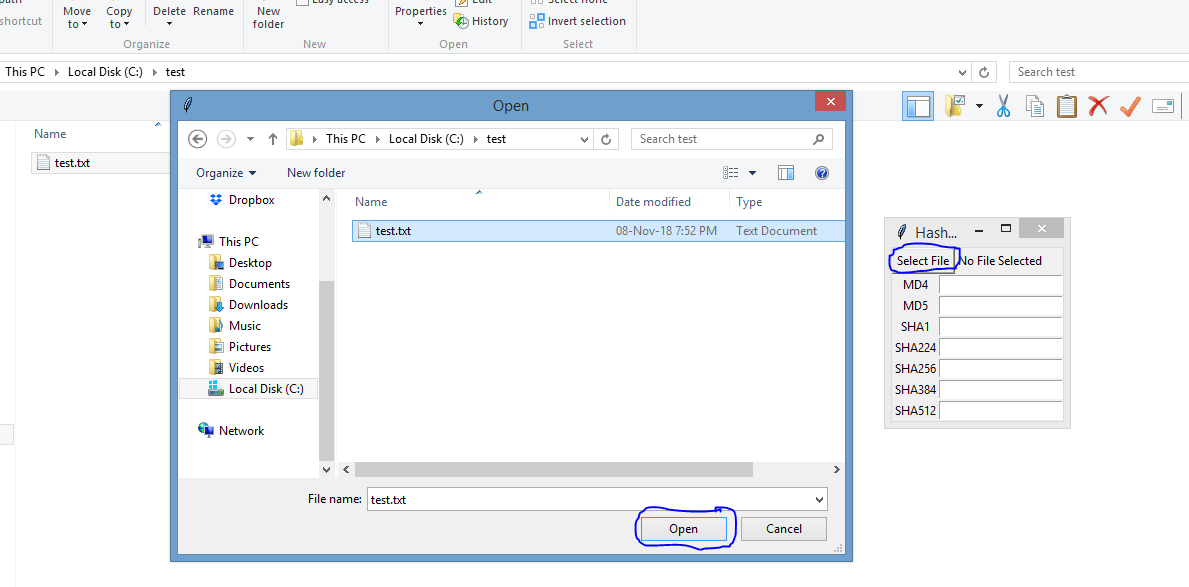
Once you choose your file the fields will be populated with the hashes of the file like so.
Conclusion
Once you have the hashes you can select the text and use CTRL + C on your keyboard to copy it and save it to a text file for later use.
Armed with these hashes you can now verify them against an official download page or portal to ensure you have the right file.
If this guide and software has helped you be sure to comment down below with any feedback and join our community for updates and check out our videos and business services.

Alessio Rigoli is the founder of AGR Technology and got his start working in the IT space originally in Education and then in the private sector helping businesses in various industries. Alessio maintains the blog and is interested in a number of different topics emerging and current such as Digital marketing, Software development, Cryptocurrency/Blockchain, Cyber security, Linux and more.
Alessio Rigoli, AGR Technology
![logo-new-23[1] logo-new-23[1]](https://agrtech.com.au/wp-content/uploads/elementor/thumbs/logo-new-231-qad2sqbr9f0wlvza81xod18hkirbk9apc0elfhpco4.png)
