Introduction
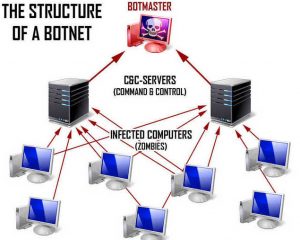
In the world of security and digital threats a botnet is a often large collection of hacked computers or servers which collectively form a network controlled by a malicious adversary. These vast networks can be leveraged to send large quantities of spam, launch DDOS attacks on popular websites or other malicious purposes such as stealing sensitive information or using your resources to mine Cryptocurrency.
Effects
Once a malicious hacker has access to a number of infected computers or servers they may choose to use these computers to launch a distributed denial of service (DDOS) attack in an attempt to flood a website with requests to crash the server.
Other times botnets can be used as an attempt to hide other illegal activity such as providing proxies for hackers to direct their cyber crime activity or malware campaigns.
Other effects of a botnet include slower networking for services affected and also potential theft of information as the botnet continuously reports back to a command and control server directed by the attacker.
How do devices get infected by botnets?
Botnets can come from a variety of places but are usually the result of downloading infected software that appears to be something else such as a free game or piece of software (usually a Trojan horse).
Other places where botnets make their way to their victims is via Phishing campaigns which are essentially malicious emails and messages that are designed to trick victims into downloading files in turn opening their devices up to botnets.
Once your computer has been infected, the hacker or hackers responsible for this attack can use it to help initiate botnet attacks. And you may be unaware that your machine has been infected.
Protecting against botnets
Most botnets look for easy targets which can include improperly configured servers using default passwords or ports, out-of-date software and malicious links or attachments in emails and other messages.
As with most malware its important to keep your system up-to-date and if you are setting up networked infrastructure change default passwords.
Other measures you can implement include setting up and running regular anti-malware scans and keeping your Operating System (Windows, macOS or Linux) up-to-date with the latest patches installed.
Conclusion
Lastly if the server doesn’t need to be public facing its almost always a good idea to take it offline to avoid becoming a target by a botnet.
Related content from our glossary:
![logo-new-23[1] logo-new-23[1]](https://agrtech.com.au/wp-content/uploads/elementor/thumbs/logo-new-231-qad2sqbr9f0wlvza81xod18hkirbk9apc0elfhpco4.png)