Introduction – What is DDoS and DoS attack and how does it work?
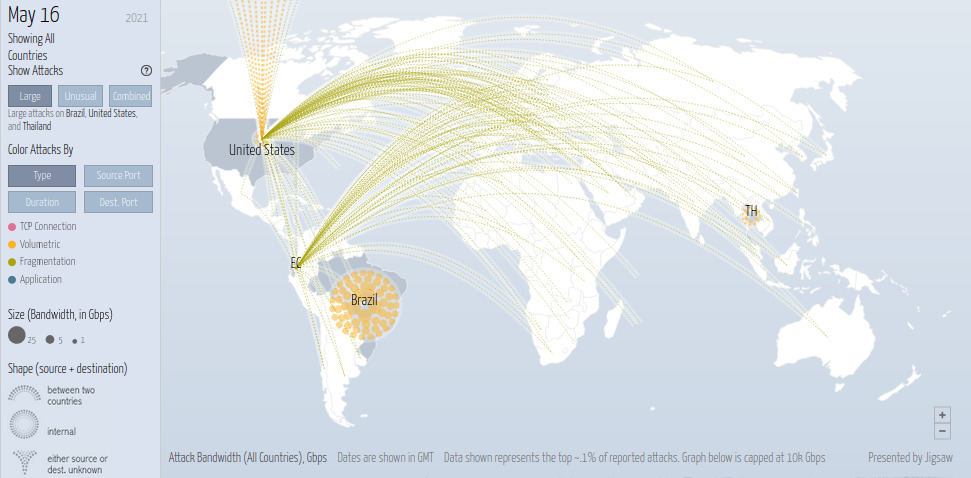
(Real-time attack map screenshot showing different DDoS attacks around the world, Source: digitalattackmap.com)
Denial of service is a type of cyber-attack in which the perpetrator attempts to make a machine or network resource inaccessible to the intended users. DoS attackers frequently target sites or services hosted on high-profile web servers, such as banks or payment gateways. A DDoS attack employs multiple unique IP addresses or machines, often from thousands of malware-infected hosts.
Multiple attack machines can generate more attack traffic than a single attack machine, multiple attack machines are more difficult to turn off than a single attack machine, and each attack machine’s behavior can be stealthier, making it more difficult to track and shut down.
Attacks may involve the forging of IP sender addresses (IP spoofing), complicating the identification and defeat of the attack. These attacker advantages pose challenges for defense mechanisms; for example, simply purchasing more incoming bandwidth may be ineffective because the attacker may simply add more attack machines.
DDoS attacks have grown in size in recent years, surpassing a terabit per second by 2016. DDoS attacks commonly include UDP flooding, SYN flooding, and DNS amplification.
Application layer attacks
An application layer DDoS attack is a type of DDoS in which attackers target application-layer processes. It differs from an entire network attack and is frequently used against financial institutions to divert the attention of IT and security personnel from security breaches.
According to Akamai Technologies’ research, there were “51 percent more application layer attacks” from Q4 2013 to Q4 2014. In 2013, application-layer attacks accounted for 20% of all DDoS attacks. Junade Ali, a Cloudflare Computer Scientist, observed that while network-level attacks continue to be powerful, they are becoming less common.
An application layer DDoS attack is carried out primarily for specific, targeted purposes, such as disrupting transactions and database access. It requires fewer resources than network layer attacks but frequently coexists with them. An attack may appear to be legitimate traffic, except that it targets specific application packets or functions.
Other types of DDoS attack variants
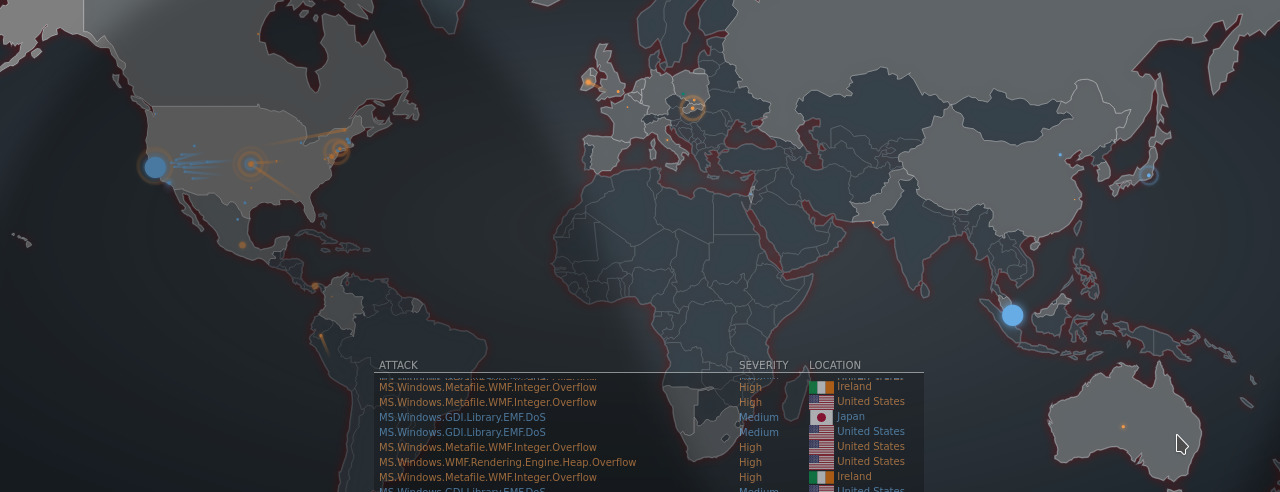
(Online attack map screenshot showing different cyber attacks globally, Source: Fortinet)
Persistent attacks
A persistent DoS (APDoS) is associated with a persistent threat and necessitates specialised DDoS mitigation. These attacks can last for weeks; the longest continuous period recorded thus far was a period 38 days.
In this scenario, attackers with continuous access to a number of extremely powerful network resources are capable of sustaining a long-term campaign generating massive amounts of un-amplified DDoS traffic.
APDoS attacks are distinguished by the following characteristics:
- Reconnaissance
- Tactical execution
- Simultaneous multi-threaded OSI layer attacks and persistence over extended periods of time
50,000 terabits of malicious traffic was used in the longest running continuous APDoS campaign to date.
DDoS-As-A-Service
Some vendors on underground hacking forums offer “booter” or “stresser” services, which have simple web-based front ends and accept payment online.
They are marketed and promoted as stress-testing tools, but they can be used to perform unauthorized denial-of-service attacks and provide technically inexperienced attackers with access to sophisticated attack tools.
Mitigation strategies
While the threat of a Denial of service can never truly be eliminated a number of methods can be deployed to significantly limit their affect and prevent the majority of attacks.
WAF Protection
WAF stands for Website Application firewall and is a mechanism put in place to act like a traditional firewall to protect websites from different attacks.
WAF systems usually include DDoS Protection and work by acting as a middle-man between the website server and requests by users.
The WAF inspects all incoming traffic and looks for suspicious patterns and then filters or blocks the traffic from hitting the web server.
In addition to protecting against Denial of service attacks they can also protect against other sophisticated hacks/intrusions such as SQL injection attempts, Brute-force attempts and XSS (Cross Site Scripting).
CDN systems
A CDN stands for a content delivery network and helps improve website performance by routing traffic through multiple high performance servers all over the world improving load times for end-users in different countries and making the online experience more convenient for them.
In addition to performance CDN’s can also compliment the functionality of a WAF by offloading a large portion of the traffic going to a web server and thus providing more “breathing room” to the server to handle incoming requests.
Conclusion
We hope you found this page to be a useful resource if so be sure to share it on social media and follow us for more. Also check out our blog and video tutorials for more content around technology.
AGR Technology is a business based in Australia providing a number of digital services helping businesses in areas such as Online Marketing, Website Design/Hosting and Software Development.
Related links from our glossary:
IaaS (Infrastructure-As-A-Service
List of some great VPN apps for torrenting
Citations & reference(s):
Wikimedia Foundation. (2021, May 25). Denial-of-service attack. Wikipedia. https://en.wikipedia.org/wiki/Denial-of-service_attack.
![logo-new-23[1] logo-new-23[1]](https://agrtech.com.au/wp-content/uploads/elementor/thumbs/logo-new-231-qad2sqbr9f0wlvza81xod18hkirbk9apc0elfhpco4.png)